AI-Generated Attacks: The Next Frontier of Cybercrime

Artificial Intelligence has changed the game for defenders and attackers alike. While AI has transformed industries and accelerated innovation, it has also opened the floodgates to a new kind of cyber threat: AI-generated attacks. These aren’t the clumsy mass emails of the past or crude malware written by amateurs. They are intelligent, automated, and frighteningly precise. As generative AI […]
Securing a Smart City’s IoT Infrastructure

Client Profile A municipal government embarked on an ambitious project to establish a smart city ecosystem by deploying a network of IoT devices. This initiative aimed to enhance public safety, optimize operational efficiency, and ensure the seamless delivery of essential services in real time. The interconnected infrastructure promised transformative benefits but also introduced new cybersecurity […]
Securing API Integration for a SaaS Provider

Client Profile A SaaS provider with a comprehensive suite of APIs for third-party developers faced growing concerns over API-related breaches. APIs were the backbone of the provider’s operations, enabling seamless integrations for clients. However, vulnerabilities in the API infrastructure posed risks to sensitive data and user trust, necessitating an immediate focus on security enhancements. Challenges […]
Strengthening Cybersecurity in an E-Commerce Platform Against APTs

Client Profile A large e-commerce platform serving millions of customers worldwide sought to protect sensitive customer records from advanced persistent threats (APTs). As a high-value target, the platform faced risks from sophisticated cyberattacks aimed at exploiting its systems, stealing customer data, and disrupting operations. Challenges The e-commerce platform’s leadership was particularly concerned about its readiness […]
How to Lock Down Your Smart Home Against Cyber Threats
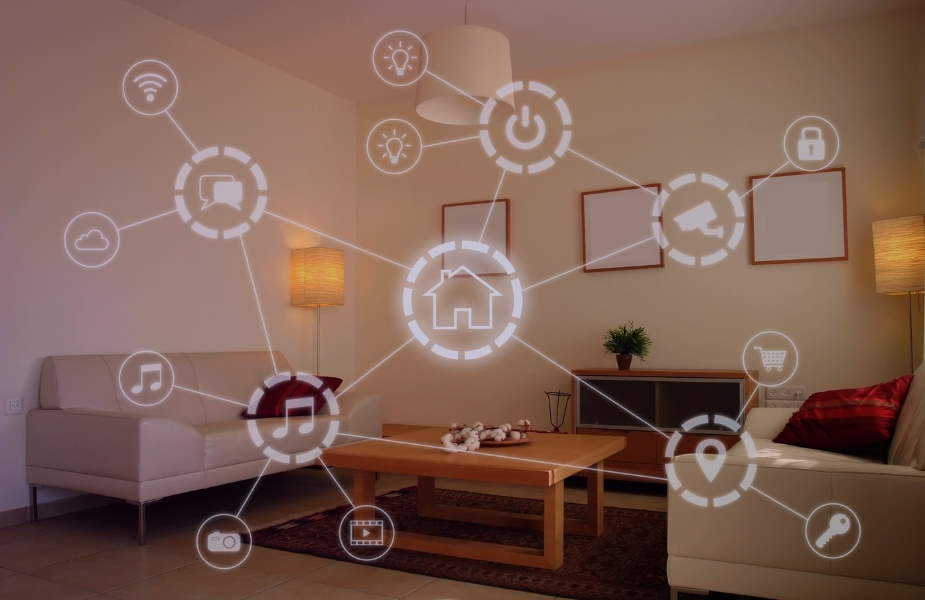
Smart homes are attractive because they offer connected efficiency and comfort. But possible security flaws grow with every gadget you include in your IoT network. From voice assistants to smart thermostats, any linked gadget might be a portal for cyberattacks. Here’s how to strengthen your smart home’s defenses and make sure your digital sanctuary stays […]
Wi-Fi Security– How to Shield Your Network from Cyber Threats

Wi-Fi networks are almost a given in both our personal and professional life in the linked world of today. But Wi-Fi’s simplicity and availability also make it a top target for hackers. This blog investigates typical Wi-Fi network weaknesses and offers best practices for wireless infrastructure security. Understanding Wi-Fi Vulnerabilities Wi-Fi networks are susceptible to […]
How Security Operations Centers Safeguard Your Digital Assets

Digital threats are persistent and developing, requiring alert and all-encompassing defenses. For many companies, the Security Operations Center (SOC) forms the center of these protections. A SOC is not only a team or a facility; rather, it has a vital role spanning several aspects of cybersecurity initiatives, including constant monitoring, detection, analysis, and response to […]
Why Grey Box Testing is Essential for Modern Cybersecurity Strategies

The requirements of contemporary digital environments are outpacing the old methodologies of black-box and white-box testing in the rapidly changing field of cybersecurity. As a result, gray box testing—a hybrid methodology that combines the best aspects of both approaches to provide a more realistic assessment of network vulnerabilities—has become increasingly popular. This blog explores the […]
How to Comply with GDPR, CCPA, and Other Global Data Privacy Laws

In our interconnected digital world, your data is more valuable—and vulnerable—than ever. As you navigate the internet, each byte of your personal information becomes a potential target for cybercriminals. This reality has spurred a global movement toward stringent data privacy regulations, with the General Data Protection Regulation (GDPR) leading the charge. Whether you’re running a […]
How Can Red Teaming Enhance Your Cybersecurity Measures?

Conventional security solutions are sometimes compared to a mediaeval castle wall in today’s ever-present cyber threat landscape—strong and formidable, but ultimately vulnerable to a determined siege. Envision a relentless adversary who is always looking for gaps in your defenses, utilizing methods that are always changing, and taking advantage of the smallest hole in your armor. […]